 22 January 2018
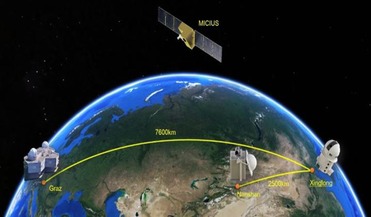
Quantum-enabled satellite passes key tests
22 January 2018
Quantum-enabled satellite passes key tests
... done via public key cryptography – an encryption scheme that uses two mathematically related, but not identical, keys; a public key and a private key. Although it is computationally infeasible to compute the private key based on the public key, the...